Secure Your Workloads with Identity-First Connectivity™ From the developers of OpenZiti
Stop wasting time on site-to-site VPNs and never-ending firewall rule changes.


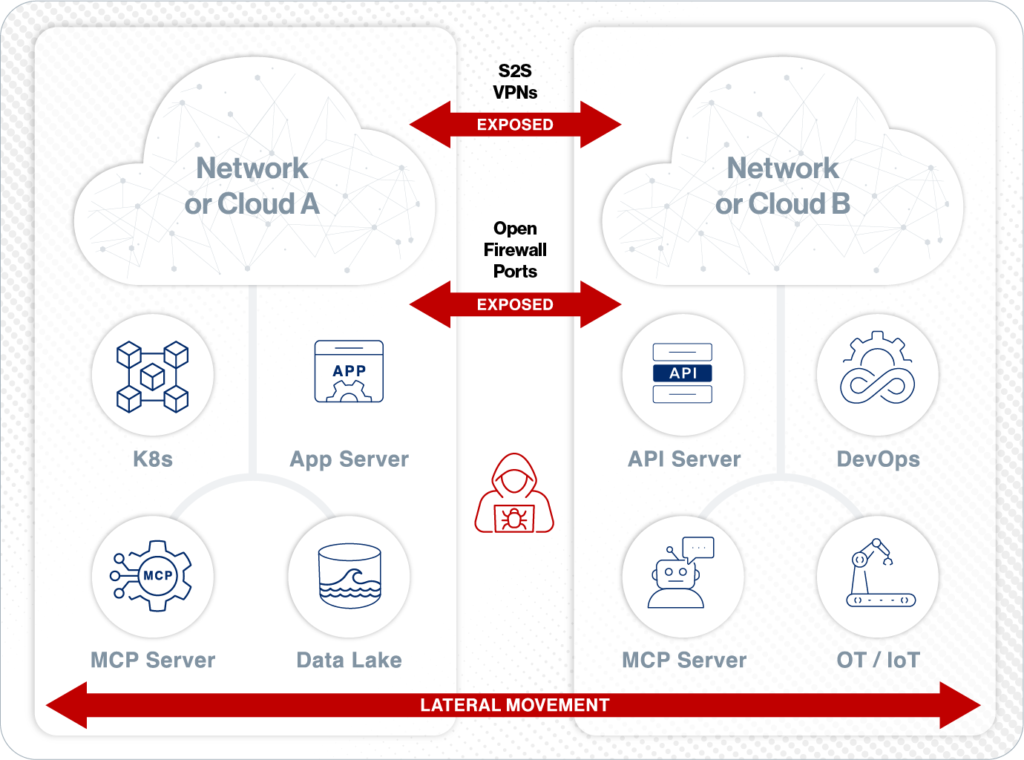
Workload deployments Create Risk and Operational Headaches
- Risky IP connectivity occurs before session authentication and authorization
- Constant firewall rule changes
- APIs exposed to entire internet
- VPNs give excessive remote access
WAFs & API Gateways
- Can’t detect a good inbound connection from a bad one.
- No identity associated with connections.
VPNs
- Painful to operate and lack fine-grained access control.
- Especially if the VPN isn’t fully under your management.
SASEs
- Only track identity inside WAN.
- Require WAFs and VPNs for higher-risk 3rd-party and external connections.
15 billion devices on the internet can connect to, scan, and exploit your attack surface.
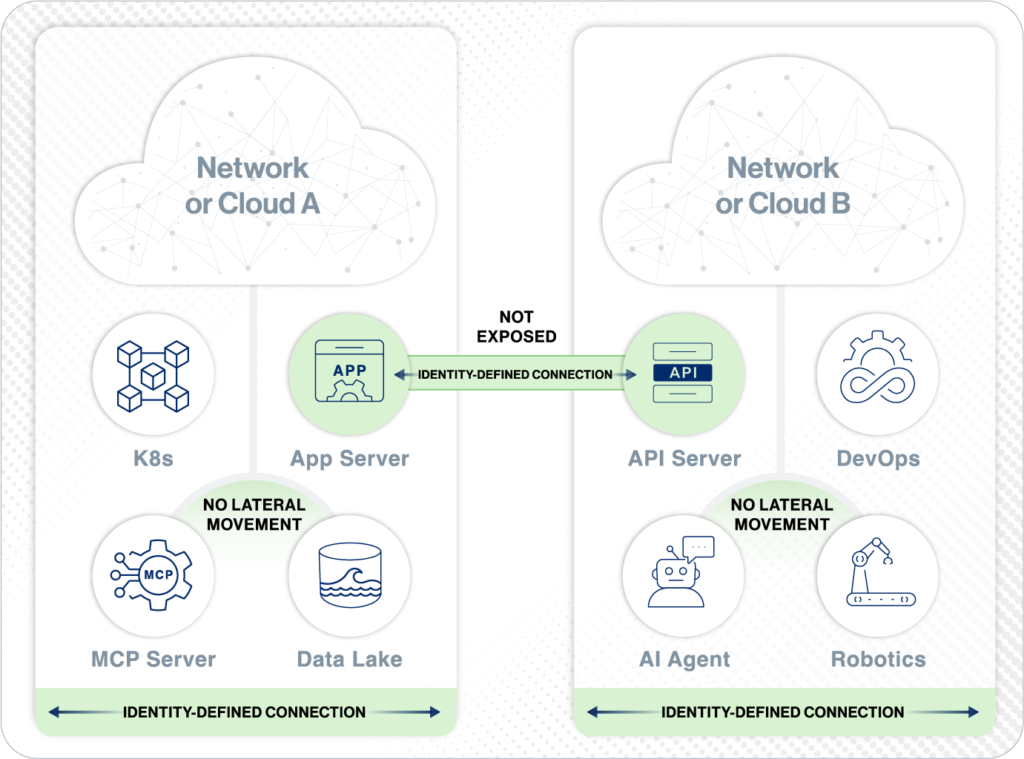
Identity-First Connectivity™is Simple and Secure
- All endpoints authenticated and authorized before any IP connectivity
- Embed Zero Trust connectivity into your workloads
- Accelerate your deployments
- Protect your attack surface
Zero Trust Workload Connectivity
Identity-based Mutual TLS
- Each connection is secured from the start.
- Each is associated with specific identities.
Outbound-Only Connections
- No VPNs to set up.
- No inbound ports to open on your firewalls.
- No ports visible to an external attacker.
Software-based Network Overlay
- Distributed routing infrastructure networks with enterprise SLAs
- Hosted by you or NetFoundry (100+ PoPs)
Simple to deploy, simple to operate, and eliminates 99.99% of exploitation risk
Compelling Use Cases
Universal Segmentation with Less Risk at Lower Cost
- Simpler, safer segmentation and micro-segmentation
- No VPN or ongoing firewall updates
- Zero-trust access based on identities and services
Replaces VPNs — Easier Management and Less Risk
- Least-privilege network access by identity and service, not port and IP – denying all by default
- Simplified operations – easy micro segmentation
- Full visibility into connected traffic by identity and service
Onboard Your Customers in Minutes, Not Weeks
- Simpler security reviews – no inbound ports
- Faster evaluations and deployments – no firewall changes
- Faster revenue recognition and easier ongoing operations
All Access Is Authorized End-to-End From the Start
- APIs are completely invisible until authentication and authorization is complete
- Less traffic to analyze
- API traffic is associated with an identity — easier to view and manage
Block Lateral Movement
- Simplified microsegmentation deployments
- Control and visibility into traffic by identity and service, not IP
- Zero trust access enables “deny by default” and least-privilege access
2000 companies use NetFoundry
Who Doesn't Love Simple & Secure?
Learn More

NetFoundry White Papers Executive Summary In today’s interconnected digital world, Application Programming Interfaces (APIs) play a crucial role in enabling data exchange and service integration across organizations. As their usage...

NetFoundry Case Studies KEO KEO International Consultants, a global leader in architecture, engineering, and project management, has been at the forefront of delivering iconic projects for over 57 years. Ranked...

NetFoundry White Papers Introduction: The State of the Managed Services Industry As digital transformation reshapes industries, managed service providers (MSPs) are increasingly tasked with securing access across diverse customer environments....

NetFoundry White Papers Zero Trust IoT The Internet of Things (IoT) has transformed both industrial and consumer landscapes by enabling interconnected devices to communicate and share data seamlessly. However, as...
Talk With Us
Learn more about securing workloads with Identity-First Connectivity™
